Setting Up Two-Factor Authentication in PeopleSoft (Part 2)
In this part of the tutorial, I have expanded on what was done in the first part by adding additional logic to the Signon PeopleCode and adding more functionality to the 2FA page. I went ahead and created an app designer project that contains all of the objects and code that serves as a proof-of-concept of how the 2FA process works as a whole. The only functionality that this project does not contain is the ability to send SMS messages. You should be able to plug and play this project into your environment.
I tried my best to explain what all is going on in the comments in the code, but here some important features that I would like to touch on:
- The 2FA process is enforced only on users that have the Peoplesoft Administrator role that do not possess a valid 2FA cookie in their browser. The code can easily be changed to challenge users for 2FA with more or different roles.
- The cookie name that gets written to the user’s browser will be in the form of PSM_2FA_TOKEN_%USERID_%DBNAME
The %DBNAME part of the cookie’s name allows the user to poses tokens for multiple environments if they wish. This assumes that this 2FA process is implemented on multiple environments.
The %USERID part of the cookie’s name is used to accommodate for multiple users that might be sharing the same browser.
- The cookie that is written to the user’s browser has a value that contains a hash of the user’s %USERID, %IP_ADDRESS, and %DBNAME.
This is what will make the cookie only valid for a specific user logging into a specific environment from a specific location. So for example, assume a user gets a 2FA token on their laptop at work to get into the CSPRD environment. The user goes home with their laptop and tries to use the previously obtained token to bypass 2FA from their home network when logging into the CSPRD environment. The user will be challenged for 2FA again since the token that they possess is only valid for their IP address at work.
Note: The details that I explained above are only really relevant if you use the “Remember This Device” functionality, otherwise the token will be deleted at the end of the session. The “Remember This Device” functionality gives the user the option to not have to do 2FA on every login. This functionality was provided for user experience purposes, but if you are looking to have a more secure solution, then do not provide this functionality to the users.
Below are the steps to get the project up and running.
UPDATE: It was discovered that this project has some compatibility issues for environments that are making use of fluid pages. See the comments section for more details.
CLICK HERE to download the project. Unzip the file and import the project into app designer.
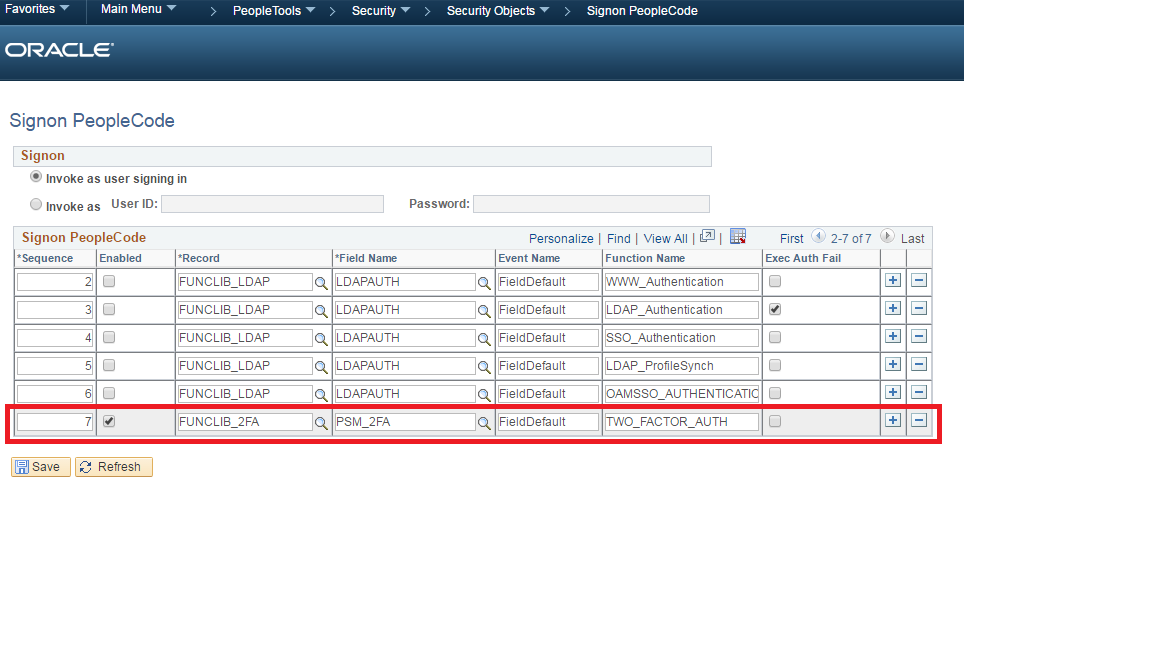
Login to PeopleSoft and add the following section to the Signon PeopleCode.
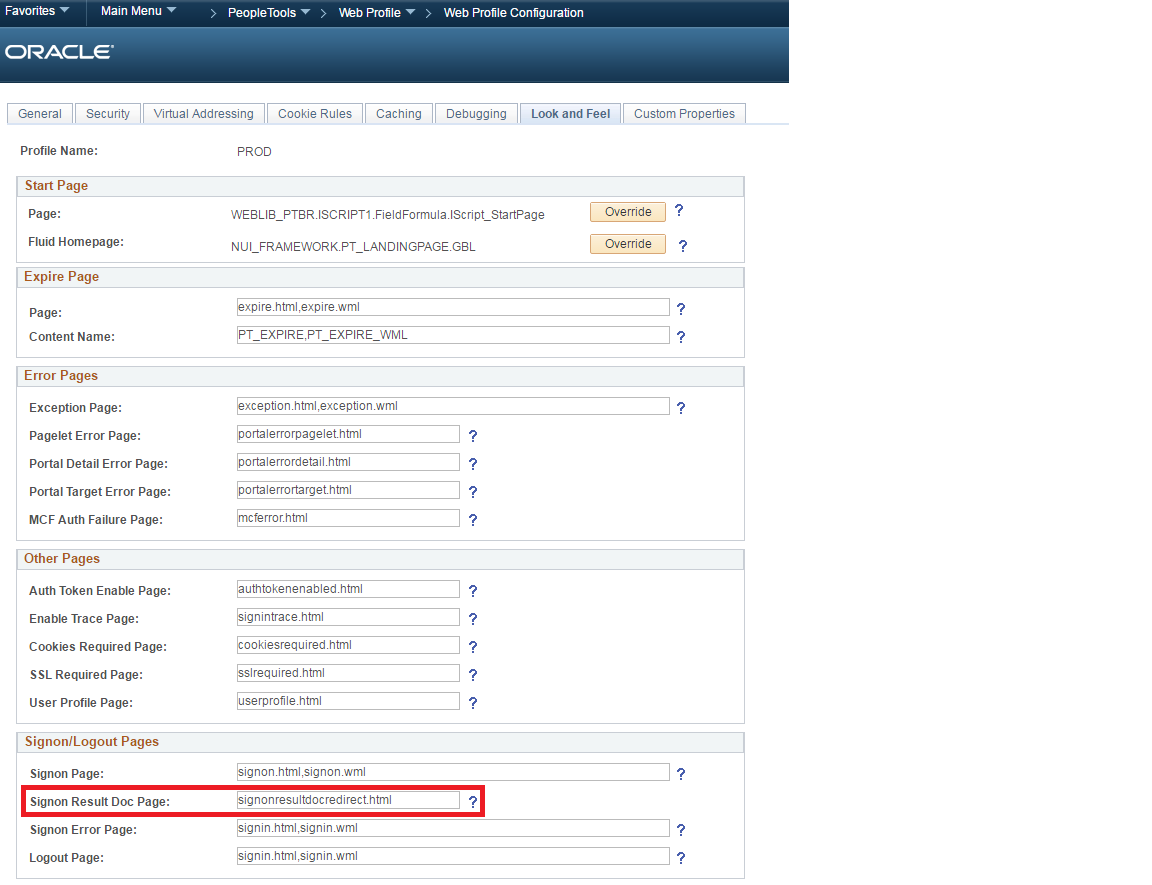
Go to the web profile configuration and set the Signon Result Doc Page field to signonresultdocredirect.html.
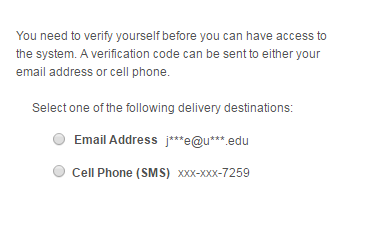
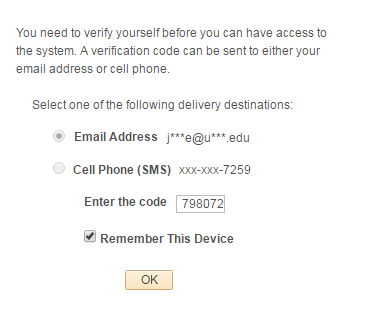
Bounce the web and app servers and log back into PeopleSoft. You should see the following page.
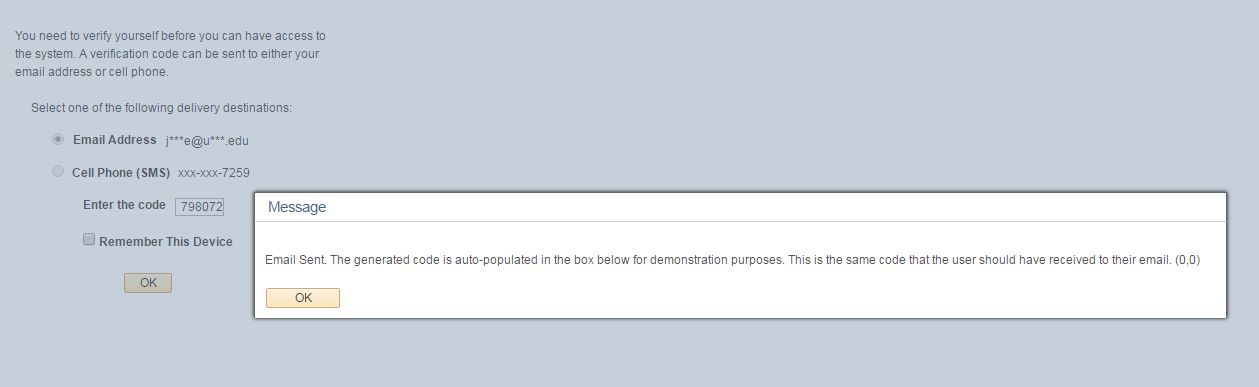
The email functionality will work if the SMTP settings are properly setup in your environment. The provided project does not include the necessary objects and code for the SMS functionality to work. Nonetheless, you can select either delivery option. Click OK on the popup prompt.
Since this is just a proof-of-concept, the application will automatically populate the code into the input box. This is the same code that the user should receive to their email or cell phone. Once you are able to ensure that you can successfully send email and SMS messages, then the auto-populate functionality should be replaced with the user having to input the code themselves. You can check the Remember This Device box if you do not want to have to do this process again on subsequent logins.
If you leave this box unchecked, then you will have to do this process again if you close the browser session and login again. Clicking the OK button should take you to the homepage and grant you full access into the system.
Important Security Considerations:
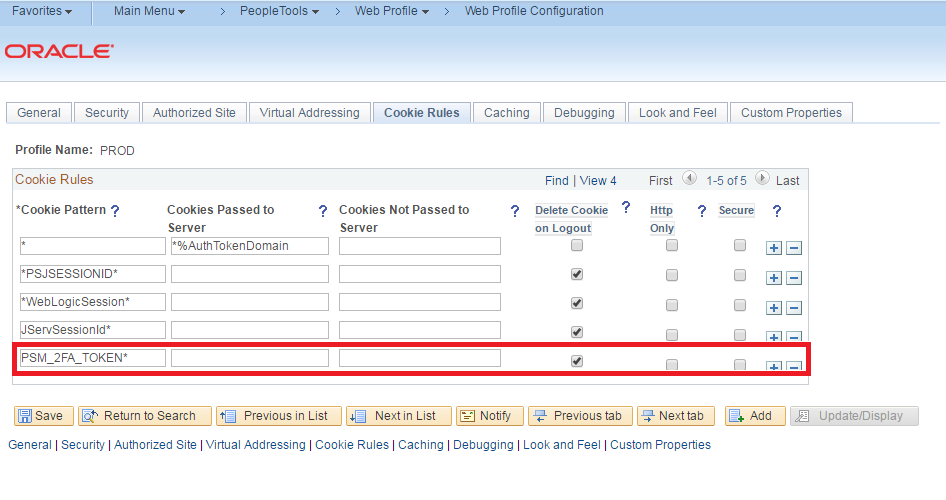
While this project may serve as a solid proof-of-concept of how you can implement 2FA in your PeopleSoft application, there are some things that I would like to point out. The first thing is that using email is not a very secure avenue to deliver the time sensitive codes. This is because, much like username and password, a user’s email account is merely something the user knows (email address and password). It is much more secure to deliver the time sensitive codes to a physical device that the user has like their cell phone or a security token (not demonstrated). The second thing is that using the “Remember This Device” functionality makes this 2FA solution less secure. This is because if a “remembered” device gets stolen, then it will potentially allow for an impostor to gain unauthorized access to another user’s account with just their username and password. It is much more secure to delete the 2FA token at the end of every session. To delete the 2FA token at the end of every session, just add the following cookie rule to the web profile: